In today's interconnected digital landscape, the need for robust cybersecurity best practices has never been more critical. As cyber threats continue to evolve and become more sophisticated, it is imperative for individuals and organizations to stay vigilant and proactive in safeguarding their data and digital assets.
This guide delves into the realm of cybersecurity best practices, offering insights and strategies to enhance your online security posture.
Importance of Cybersecurity Best Practices
Implementing cybersecurity best practices is crucial in today's digital age where cyber threats are constantly evolving. These practices are designed to protect sensitive data, systems, and networks from malicious attacks, ensuring the overall security of an organization.
Potential Risks of Neglecting Cybersecurity Best Practices
Neglecting cybersecurity best practices can expose organizations to a wide range of risks, including data breaches, financial losses, reputational damage, and legal consequences. Hackers are constantly looking for vulnerabilities to exploit, and without proper security measures in place, organizations are at a higher risk of falling victim to cyber attacks.
- Increased Vulnerabilities: Failing to implement cybersecurity best practices leaves systems and networks vulnerable to various cyber threats, such as malware, ransomware, and phishing attacks.
- Data Breaches: Neglecting cybersecurity best practices can lead to unauthorized access to sensitive data, resulting in data breaches that can have serious consequences for an organization.
- Financial Losses: Cyber attacks can result in financial losses due to theft of funds, extortion, or disruption of business operations.
Contribution of Cybersecurity Best Practices to Data Protection
Cybersecurity best practices play a vital role in safeguarding data against unauthorized access, ensuring data confidentiality, integrity, and availability. By following best practices such as implementing strong passwords, regularly updating software, and conducting security training for employees, organizations can enhance their overall data protection measures.
It is essential for organizations to prioritize cybersecurity best practices to mitigate risks and protect their valuable assets from cyber threats.
Common Cybersecurity Threats
In today's digital landscape, businesses face a myriad of cybersecurity threats that can compromise sensitive data and disrupt operations. Implementing cybersecurity best practices is essential to protect against these threats and safeguard valuable information.
Phishing Attacks
- Phishing attacks involve fraudulent emails or messages designed to deceive individuals into revealing sensitive information such as login credentials or financial details.
- Cybersecurity best practices like employee training, multi-factor authentication, and email filtering can help mitigate the risk of falling victim to phishing attacks.
Ransomware
- Ransomware is a type of malware that encrypts files or systems, demanding a ransom for their release.
- Regular data backups, network segmentation, and security patches are crucial cybersecurity best practices to prevent and recover from ransomware attacks.
Insider Threats
- Insider threats occur when employees or contractors misuse their access to sensitive information for malicious purposes.
- Implementing user access controls, monitoring user activity, and conducting regular security audits are effective cybersecurity best practices to mitigate insider threats.
Implementing Strong Password Policies
When it comes to cybersecurity, implementing strong password policies is crucial in protecting sensitive information and preventing unauthorized access to systems and data.Designing a strong password policy for an organization involves setting guidelines for creating secure passwords and enforcing regular password changes to enhance security measures.
It is essential to emphasize the importance of password complexity, length, and uniqueness to reduce the risk of password guessing or brute force attacks.
The Role of Password Complexity and Regular Changes
- Encourage the use of complex passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
- Set minimum password length requirements to ensure passwords are not easily compromised.
- Regularly prompt users to change their passwords to prevent unauthorized access in case of a security breach.
Multi-Factor Authentication for Enhanced Security
Multi-factor authentication adds an extra layer of security by requiring users to provide two or more forms of verification before granting access to accounts or systems.
- Implement multi-factor authentication for critical systems or accounts to mitigate the risk of unauthorized access even if passwords are compromised.
- Utilize methods such as SMS codes, biometric scans, or hardware tokens to enhance authentication processes.
Employee Training and Awareness
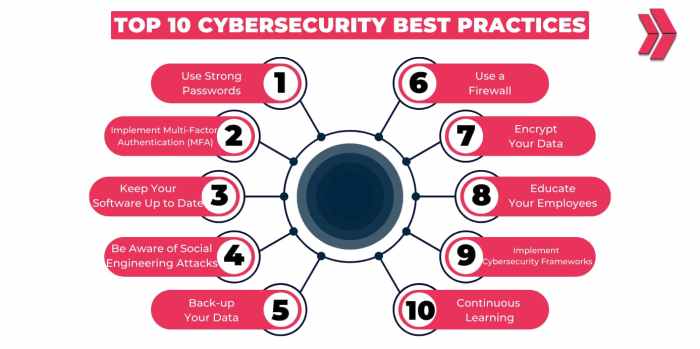
Employee training and awareness are crucial components of a strong cybersecurity strategy. By educating employees on cybersecurity best practices, organizations can mitigate risks and prevent potential threats from compromising sensitive data.
Creating a Training Program
- Develop a comprehensive training program that covers the basics of cybersecurity, including common threats and best practices.
- Include examples of social engineering techniques, such as phishing emails, pretexting, and baiting, to help employees recognize and respond to potential threats.
- Utilize interactive training modules, simulations, and real-life scenarios to engage employees and reinforce learning.
Importance of Ongoing Training
- Regularly update training materials to reflect the latest cybersecurity trends and threats.
- Encourage employees to stay informed about cybersecurity risks through newsletters, workshops, and online resources.
- Conduct periodic assessments and tests to evaluate employees' knowledge and awareness of cybersecurity best practices.
Securing Network Infrastructure
When it comes to cybersecurity, securing your network infrastructure is crucial to protect your organization from cyber threats. By implementing best practices and utilizing the right tools, you can create a robust defense system to safeguard your network.Zero Trust Security:Zero trust security is a concept that promotes the idea of not trusting any entity inside or outside your network by default.
This approach requires verification and authentication for all users and devices trying to access the network, regardless of their location. By adopting a zero trust security model, organizations can minimize the risk of unauthorized access and potential security breaches.Role of Firewalls, Encryption, and Intrusion Detection Systems:Firewalls act as a barrier between your internal network and external threats, filtering incoming and outgoing traffic to prevent unauthorized access.
Encryption ensures that data transmitted over the network is secure and unreadable to unauthorized users. Intrusion Detection Systems (IDS) monitor network traffic for suspicious activities or potential security threats, alerting administrators to take action promptly.
Best Practices for Securing Network Infrastructure
- Regularly update and patch all network devices and software to address vulnerabilities.
- Implement strong access controls and user authentication mechanisms to restrict unauthorized access.
- Segment your network to isolate critical assets and limit the impact of a potential breach.
- Monitor network traffic and behavior to detect anomalies and potential security incidents.
- Educate employees on cybersecurity best practices and the importance of maintaining network security.
Incident Response and Disaster Recovery
Developing an incident response plan is crucial in ensuring a timely and effective response to cybersecurity incidents. This plan Artikels the steps to be taken when a security breach or incident occurs, helping to minimize the impact on the organization.
Steps for Developing an Incident Response Plan
- Establish a dedicated incident response team with clear roles and responsibilities.
- Identify and prioritize critical assets and data that need protection.
- Create a detailed incident response policy outlining procedures for detection, containment, eradication, and recovery.
- Implement monitoring tools and technologies to detect and alert on potential incidents.
- Regularly review and update the incident response plan based on lessons learned from drills and real incidents.
Importance of Regular Drills and Testing
Regular drills and testing of incident response procedures are essential to ensure that the team is prepared to handle a security incident effectively. This practice helps identify gaps in the plan, improve response times, and enhance overall incident management capabilities.
Role of Disaster Recovery Plans
Disaster recovery plans play a critical role in minimizing the impact of cybersecurity incidents by outlining procedures for restoring systems and data after an incident. These plans ensure business continuity and help organizations recover quickly from disruptive events, reducing downtime and financial losses.
Final Wrap-Up
As we conclude this exploration of cybersecurity best practices, it becomes evident that a proactive approach to cybersecurity is paramount in today's digital age. By implementing the strategies and recommendations Artikeld in this guide, you can fortify your defenses against cyber threats and protect your valuable information from potential breaches.
Stay informed, stay vigilant, and stay secure in the ever-changing landscape of cybersecurity.
Question & Answer Hub
How often should passwords be changed?
Passwords should ideally be changed every 60-90 days to reduce the risk of unauthorized access.
What is the significance of multi-factor authentication?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification before accessing an account or system.
Why is ongoing employee training important for cybersecurity?
Ongoing training helps employees stay informed about the latest cybersecurity risks and equips them with knowledge to identify and respond to potential threats effectively.













